Data security is crucial to keeping a business up and running. Without the proper data, the organization cannot make the correct business decisions. When securing the data, as well as the systems that process, store, and transmit this data, there are three main concepts to keep in mind and they are confidentiality, availability, and integrity. Confidentiality means that only the people who are supposed to view or access the data have that ability. It also includes ensuring that the source of the information is the correct source. Availability means that the data is always accessible. This means that system crashes should be kept at a minimum. Finally, there’s integrity. This basically means that the data is accurate and consistent. This verifies that data in transit hasn’t been changed.
Cybersecurity Outreach
As part of my information security coursework, I was required to go out into the community and teach about the fundamentals of security. For this project, I delivered it my managers at McAlisters’s Deli since they constantly deal with customer data. Therefore, ensuring security of this data is extremely important. They were very welcoming of this new information and have begun to take measures to follow these steps to securing customer data, as well as their own personal data.


Database Security
In a large organization, it can be tough trying to secure all of the different systems and user’s permissions. Active directories allow for the storage of these systems into a domain, and within these domains are organizational units. The existence of these organizational units allows for the admins to create and distribute settings and rules under group policies. In this example, I created several users within an organizational unit and attempt to change the group policy in order to increase password complexity and length.
In this screenshot I show proof that the users I created (sql user, sql user 1, and sql user 3) are located within the sqlgroup OU and that the sqlgroup OU is stored in the Groups OU.

This assignment deals with user roles and how to manage them. In this assignment I assigned a user to a database role using user mapping, and created a custom database role and application role.
Network Security
Securing data in transit is also extremely important to the CIA of data. In this example, I first perform a ping sweep of a range of networks attempting to find a available hosts. I find a host and then perform a port scan, searching for any open ports on the machine. For this assignment, I used Nmap on Kali Linux to perform the ping sweep, as well as the port scan. I also used Wireshark to capture the packets going back and forth between my machine and the host computer.
In this screenshot I have entered a command into Kali Linux to display the IP address of the virual machine.
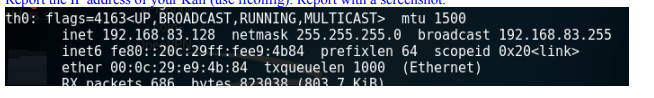
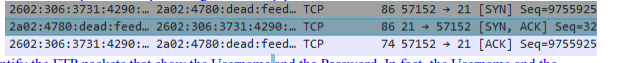
Here I have used Wireshark to find the first three TCP packets of the initial 3-way handshaking.
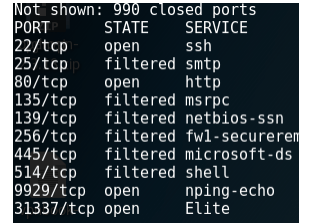
In this screenshot from the assignment, I have entered a command in Kali to perform an Nmap port scan of a Windows machine.
As part of my network security class, we had to perform in the National Cyber League, which presents the user many challenges in different areas of network security. For this assignment, I had to choose two different challenges to complete and I chose the Network Packet Analysis and Encryption challenges. The Network Packet Analysis challenge required the use of Wireshark to search through a sequence of packets to answer the questions. The encryption analysis required decoding of hex and binary values into plaintext.
Using Wireshark, I have found the packet of the first successful log on.

Security Research
Learning about security would be pointless if you didn’t learn about the various types of threats and attacks that are prevalent throughout the internet. In this assignment, myself and a partner, decided to research Distributed Denial-of-Service attacks to understand how you could possibly stop, or at least mitigate, such an attack. A distributed denial-of-service attack is one where the server is overwhelmed with requests to connect from many different sources.
Computer Forensics
Along with the network and database security, I have also learned a little bit about computer forensics and how to artifacts to identify user behavior. In this project, I was given a hard drive and had to search for artifacts in the link and jump lists, registries, recycle bin, and the event logs.